Organizations face increasing pressure from regulators and their own customers to fully protect data. The threat of a costly data breach always looms, and businesses must take their role as data stewards seriously. Yet, effective data security doesn’t mean the data has to sit untouched in a vault.
De-identifying your and your customers’ data of sensitive elements fully protects the data as it moves across diverse cloud and on-premises environments—enabling your organization to use data to inform AI, Loading...machine learning, analytics, and any other data-driven initiative that will help you successfully compete in the digital world.
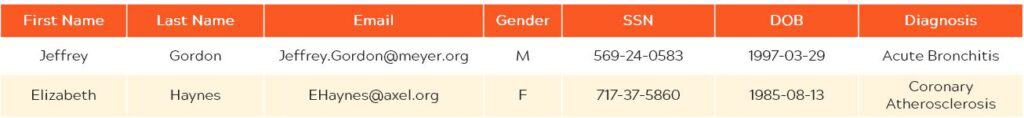
Original data
Here’s what your data looks like unprotected. It’s cleartext.
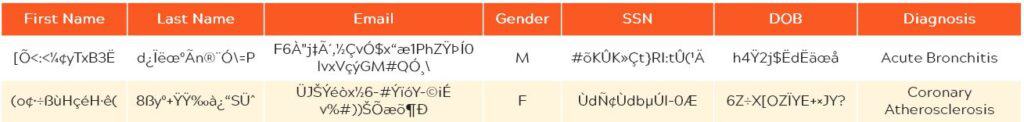
Pseudonymization: Encryption and Tokenization
One method to de-identify this data is pseudonymization. There are two effective ways to pseudonymize: encryption and tokenization.
Encryption uses mathematical algorithms and cryptographic keys to change data into binary ciphertext.
Tokenization converts cleartext data into a string of characters based on random values.
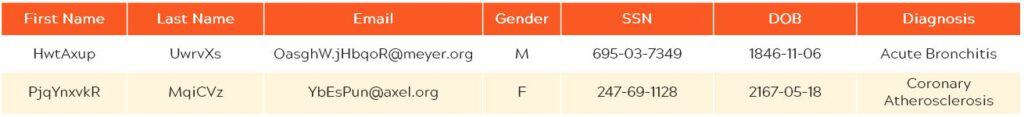
Pseudonymizing data doesn’t mean it’s gone forever: the process is reversible, allowing authorized users to view and manage the protected data afterwards. Also, tokenization maintains data type and length: when the user needs the original data, it can be restored to its original state.
Anonymization
Anonymization strips sensitive elements from data, irreversibly protecting it.
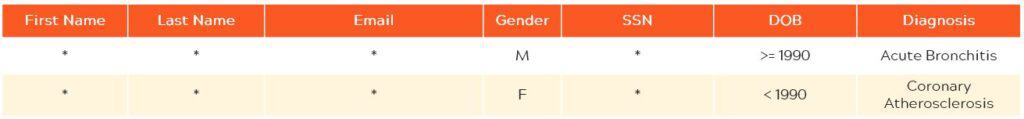
Organizations might want to anonymize data for a variety of reasons, especially to participate in data exchanges and marketplaces where data can be shared and monetized. Also, when companies want to share privately company-to-company or with SaaS systems, such as Workday or Salesforce, irreversible protection methods might be required.
Make the most of data by de-Identifying sensitive elements
De-identified data is ready to be immediately used in AI, analytics, machine learning, and other business applications without disclosing identities, sensitive personal information, and intellectual property.
De-identification meets stringent compliance, privacy, and regulatory requirements, including GDPR, PCI, PHI, HIPAA, and PII mandates.
When running Protegrity operations directly on Exasol’s high-performance Loading...in-memory engine, you can protect large amounts of data within seconds instead of minutes or hours. And your data is protected at all times, no matter where it is: cloud and on-premises systems, applications, and files—even if it travels outside to a fully unprotected environment.
De-identification is compatible with Exasol for all existing and future applications. The Protegrity Database Protector for Exasol seamlessly enhances the security of any Exasol warehouse with industry leading high-performance encryption, tokenization or dynamic data masking combined with centralized policy-based protection, auditing, and reporting.
Protect data in-motion and at rest
Protegrity secures data where it resides—not just when it is in motion. Rather than creating copies of data or just masking it—leaving the source data vulnerable, as some security platforms do—Protegrity protects the actual data. The Protegrity Data Protection Platform closes security gaps and simplifies the management of policies. With a cohesive approach to data protection—including de-identification of sensitive data elements—businesses can extract transformative insights to fuel growth, knowing sensitive data is always secure.